AWS' policy language is notoriously challenging. As you build out your infrastructure, you commonly run into situations where two components ought to be able to communicate, but can’t. In an attempt to unstick your development progress, you reach for progressively larger and larger hammers as you broaden the permissions in your policies. You promise yourself that once everything is working, you will come back and lock things down to just what is necessary. The accumulation of this type of technical debt is a common cost of product development.

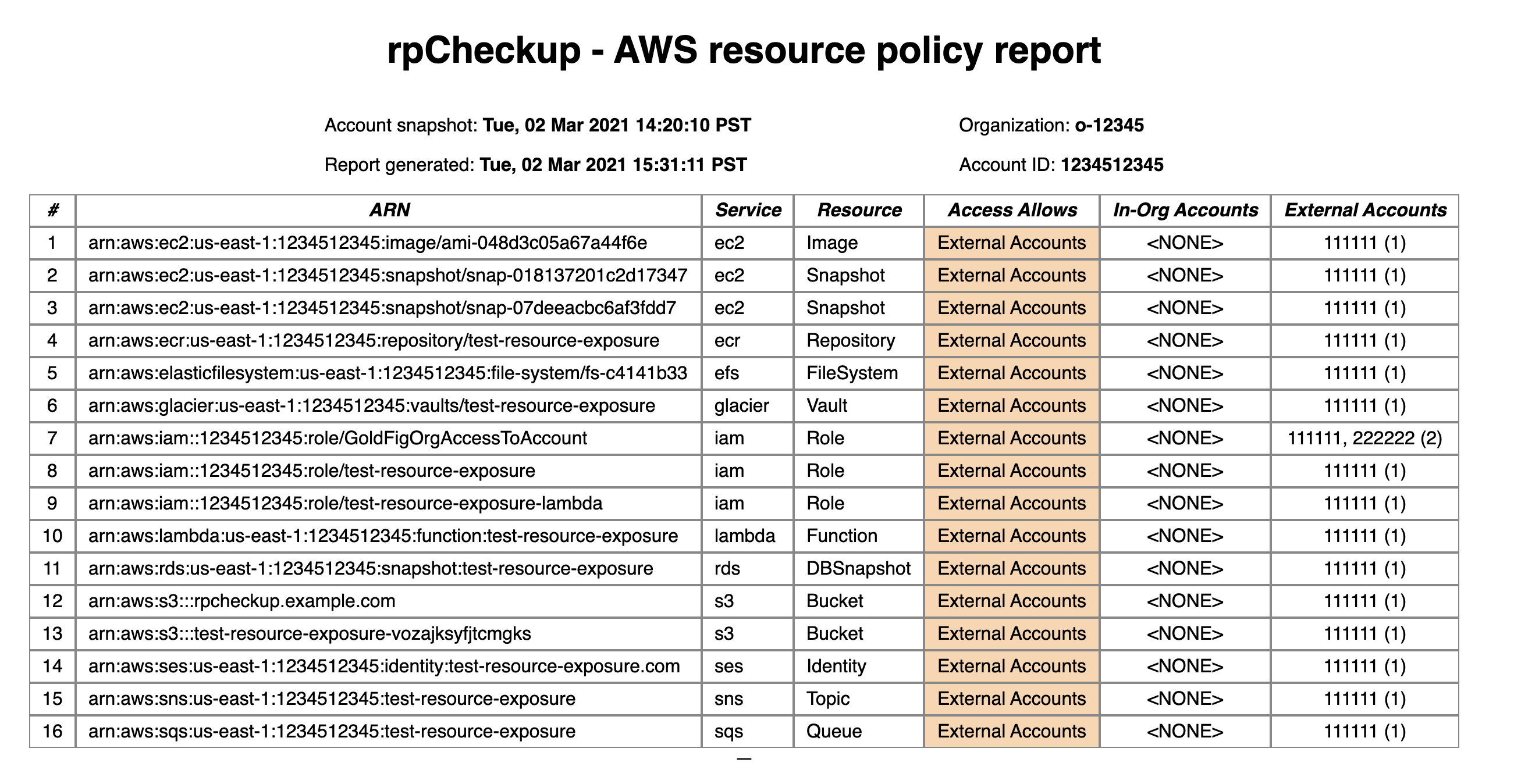
Avoiding the predictable conclusion of this scenario is a matter of visibility. If you can see the problem, it’s easier to prioritize fixing it. Several tools exist to help with assessing IAM policies. AWS has Access Analyzer. Cloudsplaining is also a good starting point for assessing your exposure. Today, we’re adding to this mix with rpCheckup. rpCheckup covers resource policies specifically, looking for outside access to your resources. This is what it looks like, run against an account exploited by Endgame:
Any resources that show up as externally accessible or public ought to be recognizable to you. Some examples include intentionally public buckets and roles used by 3rd party vendors. For example, if you are a Gold Fig customer, you will see an IAM Role that allows access from Gold Fig’s account. Things to watch out for include resources that are unintentionally public, like an SNS Topic or SQS Queue, and access by accounts that you don’t expect.
We hope this will help teams follow through on their intentions to properly secure their infrastructure, along with other tools in the ecosystem.
Gold Fig can help you with your resource policies, IAM policies, and more.