If you imagine your organization as a sea-faring vessel, infosec’s goal is to ensure the boat can survive krakens or canon-wielding pirates and successfully complete its journey. If you ignore the existence of sea terrors, you may not make it to your destination unless Poseidon grants you merciful passage. If you prioritize defense above your vessel’s mission, you will find yourself aboard a battleship that is entirely inadequate for transporting revenue-generating cargo. — On YOLOsec and FOMOsec, Kelly Shortridge
Startups are all about focusing on the right thing at the right time. Juggling everything through the fog of product development, managing your runway, and growing a team are tough on their own. Unless it’s a primary piece of your product offering1, CTOs rarely prioritize security in the early days of a startup. Contemporary startups have the benefit of the accumulation of best practices becoming more commonplace and accessible: appsec best practices get caught in code reviews, infrastructure providers bias toward secure defaults, engineers are accustomed to using things like password managers and MFA apps. However, beyond that, founders in search of product-market-fit do not have the cycles to focus on infosec. It’s a type of technical debt that is accrued while focus is elsewhere.
As your traction begins to grow, paying down technical debt becomes a recurring focus for your team. This typically takes the form of application, infrastructure, and ops related debt. As a CTO, preventing the CEO from accidentally deleting the production database is a more immediate threat than a targeted attack. Improving your processes to prevent shooting yourself in the foot will pay immediate dividends. Solving your startup’s problems around self-incurred outages and data loss are more pressing than infosec.
There is no positive benefit when it comes to security — the best outcome you can expect and actually aim to get is a reduction of negative impact. Your product or customer experience is not directly improved by an increased security posture. However, the amount of downside is unknown and potentially large. This is what will start keeping the founders up at night. Peace of mind. It all changes when there’s now something at stake. Reputation. Customer trust. Reliability. Anything that’ll erode that hard earned product market fit. Any bad press that’ll reduce the slope of your week over week growth.
This is the right time a startup should start prioritizing infosec.
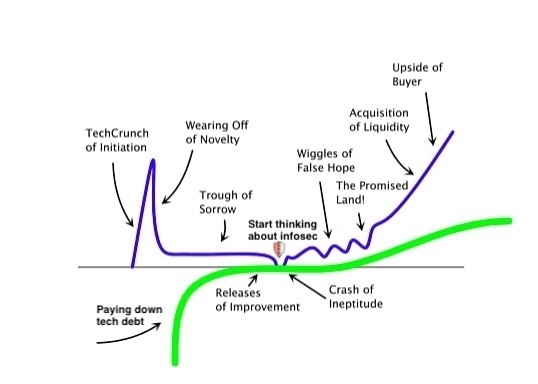
For all the fear-mongering related to security that’s out there, even for well-established companies, security’s priority with respect to product can be a tricky thing to pin down. Is it just another sign off like legal review? Was it just bolted on because an enterprise sale necessitated it? The earlier your startup weaves infosec into the engineering culture, the longer head start you have in paying down security related technical debt. The dividends you get from this yields a resilient engineering organization which treats security as a partner in building the product and not an impediment.
Gold Fig series on infosec basics
- Do The Basics First - What To Check Before Launching on AWS
- Mediocre persistent threats: infosec basics for startups (part 2)
- Mediocre persistent threats: infosec basics for startups (part 3)
- The DevOps Security Checklist Redux
- The SaaS CTO Security Checklist Redux
- The Personal Infosec & Security Checklist
1 Some other scenarios where security is an early priority for a startup. 1) Product mandated security considerations: it’s in the value prop of the product, mandated by a vendor (i.e. using the GMail API requires an external security audit); 2) Externally mandated security considerations: Government or industry regulatory considerations; product penalties if you are non-formant (i.e. amount of loan origination that can be a penalty if your banking startup is fails external security audits); 3) Customer mandated considerations: AWS GovCloud, SOC2, etc — it’s forced by the need to acquire specific customers and/or drive sales.



